In a recent cybersecurity discovery, experts have uncovered a deeply concerning attack campaign putting everyday users in Brazil and beyond at risk.
Since the beginning of 2025, a super stealthy browser-based malware operation now dubbed Operation Phantom Enigma has infected 722 users across Latin America and other parts of the globe.
The campaign utilizes a malicious browser extension aimed at Chromium-based browsers such as Google Chrome, Microsoft Edge, and Brave.
Its primary objective is to steal banking credentials and authentication tokens from unsuspecting users. I would say a definite legit reason to be super cautious and alarmed by the sophistication used 😯
- Attack Method – Phishing Emails and Fake Invoices
- Infection Flow – Multi-Stage Malware Deployment
- Escalation and Persistence – Staying Hidden in Plain Sight
- Dangerous Commands Executed by the Malware
- Targeted Browsers and Malicious Extension Identifiers
- Banking Threat – Real Time Credential Theft
- Broader Infection Strategy – Beyond Browser Extensions
- Traces Left Behind – EnigmaCyberSecurity Identifier Discovered
- Intentions and Motives Behind the Campaign
- Conclusion – Operation Phantom Enigma
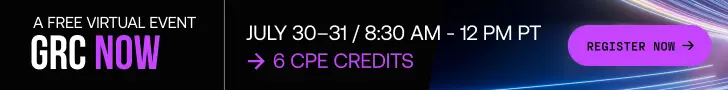
Attack Method – Phishing Emails and Fake Invoices
The attack starts with carefully crafted phishing emails disguised as invoices, often sent from compromised business servers.
This tactic significantly increases the chances of victims trusting and opening the emails.
These messages typically encourage users to download a file or open a malicious attachment, both of which are booby-trapped with malicious code.
Infection Flow – Multi-Stage Malware Deployment
Once the victim downloads and executes the file, a batch script is activated. This script fetches and runs a PowerShell script designed to:
- Detect if it’s running in a virtual environment.
- Check for the Diebold Warsaw security plugin, widely used in Brazilian banking transactions.
This check helps the malware target users more likely to engage in online banking, thus increasing the campaign’s financial impact.
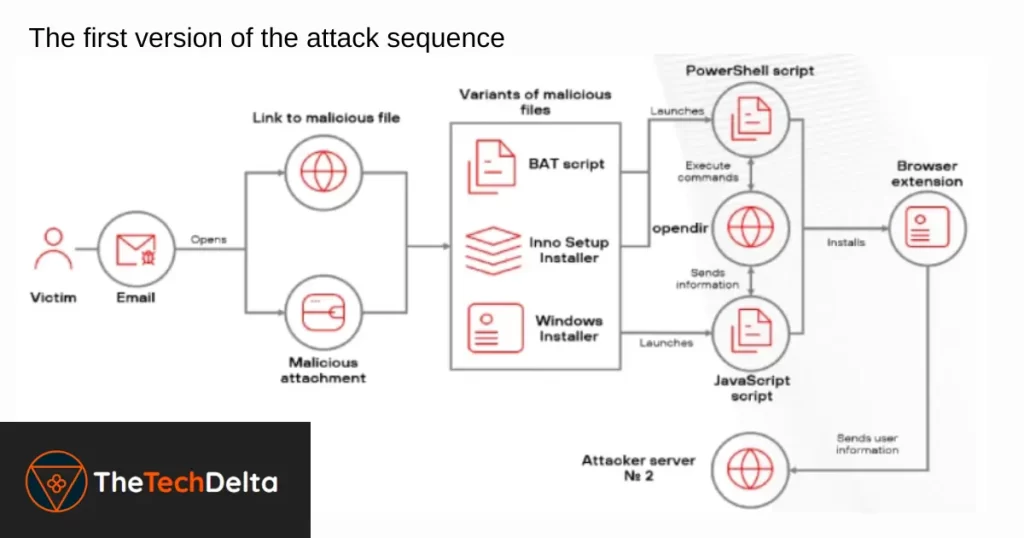
Escalation and Persistence – Staying Hidden in Plain Sight
The PowerShell script goes a step further by:
- Disabling User Account Control (UAC).
- Setting the malware to relaunch automatically after system reboot.
- Connecting to a remote command-and-control (C2) server to receive further instructions.
Dangerous Commands Executed by the Malware
Once installed, the malware is capable of executing several dangerous commands in a sophisticated way 😯 including…
PING: Confirms the malware is active.DISCONNECT: Terminates the process on the victim’s system.REMOVEKL: Uninstalls the script.CHECAEXT: Checks for the malicious browser extension.START_SCREEN: Forces browser extension installation via the Windows registry.
Targeted Browsers and Malicious Extension Identifiers
Researchers found that the attack utilized browser extensions with the following IDs I mentioned below. Check these
nplfchpahihleeejpjmodggckakhgleeckkjdiimhlanonhceggkfjlmjnenpmfmlkpiodmpjdhhhkdhdbnncigggodgdfli
Although these extensions have been removed from the Chrome Web Store, their impact has already reached multiple countries including Brazil, Colombia, Mexico, Vietnam, the Czech Republic, and Russia.
Banking Threat – Real Time Credential Theft
The malicious browser add-on activates when users visit banking sites like Banco do Brasil, capturing:
- Authentication tokens
- Sensitive information through malicious JavaScript
Commands like WARTEN (Wait) and CODE_ZUM_LESEN (Code to Scan) appear in German, suggesting either the use of European-developed code or misdirection.
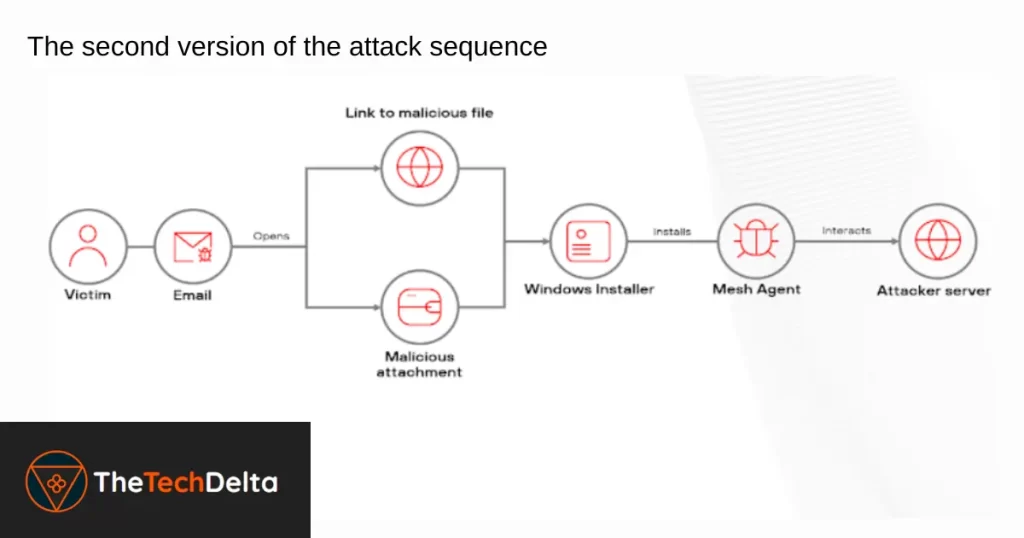
Broader Infection Strategy – Beyond Browser Extensions
Operation Phantom Enigma doesn’t stop with browser extensions. In some cases, attackers swap the initial batch script with Windows Installer (.msi) or Inno Setup (.exe) files.
These installer variants aim to:
- Deploy the malicious extension
- Or alternatively, install remote access tools such as:
- MeshCentral Agent
- PDQ Connect Agent
These tools enable the attackers to control systems remotely, expanding their capabilities to exfiltrate data or monitor user behavior in real time. Definitely troublesome to a great extent.
Traces Left Behind – EnigmaCyberSecurity Identifier Discovered
Further investigations by Positive Technologies revealed open directories used by attackers. Some links contained an identifier labeled:
<victim-domain>/about.php?key=EnigmaCyberSecurity
This identifier provides a digital footprint suggesting coordination and possibly links to other cybercriminal operations.
Intentions and Motives Behind the Campaign
Cybersecurity analyst Klimentiy Galkin emphasized that the main aim of this campaign is to steal banking credentials from everyday Brazilian users.
Interestingly, companies appear to have been infected not for direct exploitation, but to distribute phishing emails more discreetly. This strategy allowed attackers to masquerade as legitimate organizations while launching mass-scale infection campaigns.
Conclusion – Operation Phantom Enigma
Operation Phantom Enigma is a disturbing reminder of the ever-evolving tactics used by cybercriminals. From phishing schemes to browser extensions and remote access tools, attackers are leveraging multi-layered infection chains to compromise everyday users and financial institutions.
If you’re a cyber enthusiast or an everyday internet user, ensure your systems are protected with up-to-date antivirus solutions, avoid opening unknown attachments, and always verify email senders before clicking on any links. This is a must irrespective of what you do on online.
The. cyber threat landscape in Latin America is rapidly growing, and this campaign proves that browser-based attacks are no longer just a possibility they’re a reality.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on X (formally Twitter) and Instagram to stay informed about emerging threats and developments.
Also Read : Global Ransomware Crackdown Seizes €3.5M and Shuts Down 300 Servers